3
2013
Bank websites attacked
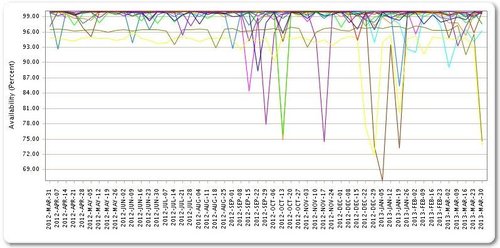
Yet again the US business industry has underestimated their attackers, and they are slowly losing this war. Major U.S. bank websites have been offline a total of 249 hours in the past six weeks, and hackers are not doing all that they can. At most they are at around 60%-70% full throttle, and there may be good reason. To learn about someone’s defenses, the easiest way is to make them use them. You find out what they have, how they are going to use it, and if they can actually fight off your basic offense. Once you have that figured out, your plan of attack is much easier.
A few months back, Bank of America, Wells Fargo, PNC and a number of other banks suffered hours-long website outages. A group calling itself Izz ad-Din al-Qassam Cyber Fighters released an anonymous statement saying it was attacking banks in sympathy with real-world protestors who were reacting to an anti-Islam film that had been posted online. No one really believes that a perceived insult over a Web movie is the attackers’ motivation, as the al Qassam messaging has stated. Though some considered that it might be the work of attention-seeking teen-aged hackers, they would likely have grown bored, or run out of resources, long ago.
In the fall, national security officials speaking on background told several media outlets, including NBC News, that they suspected the Iranian government was behind the attacks. It seems certain that an organized group, with both a political motive and the ability to fund the operation, is to blame.
Yet somehow, a few still believe it is just a nuisance. Michael Smith, director of the customer security incident response team at Akamai Technologies Inc., which provides website performance optimization and security for some of the companies targeted in the attacks, points out that customers have plenty of other ways to manage their money, and the outages haven’t amounted to much more than an irritant.
Big business, and many small businesses, need to prepare themselves for the worst. I am not talking “prepping” like the tv show, but being able to either fend off an attack or to recover quickly. Backup upon backup is one way, redundant systems, and I do believe in “whitehat” hacking. I have talked about this before, and believe it can really work. It is kind of a “let me teach you a lesson young whipper snapper” approach, but it can work. It has been used in military work for centuries (we have spies for a reason), and in business for quite awhile as well (ever hear of a non disclosure agreement?). I hope they start doing this soon, and they need to get students ready for it.
 An article by paradise
An article by paradise








Hey! I know this is kinda off topic but I’d figured I’d
ask. Would you be interested in trading links or maybe guest authoring a blog post or vice-versa?
My website discusses a lot of the same subjects as yours and I believe
we could greatly benefit from each other. If you might be interested
feel free to shoot me an e-mail. I look forward to hearing from you!
Fantastic blog by the way!